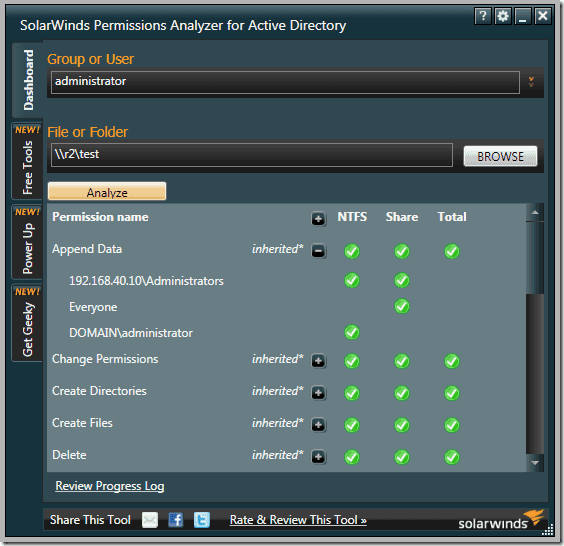
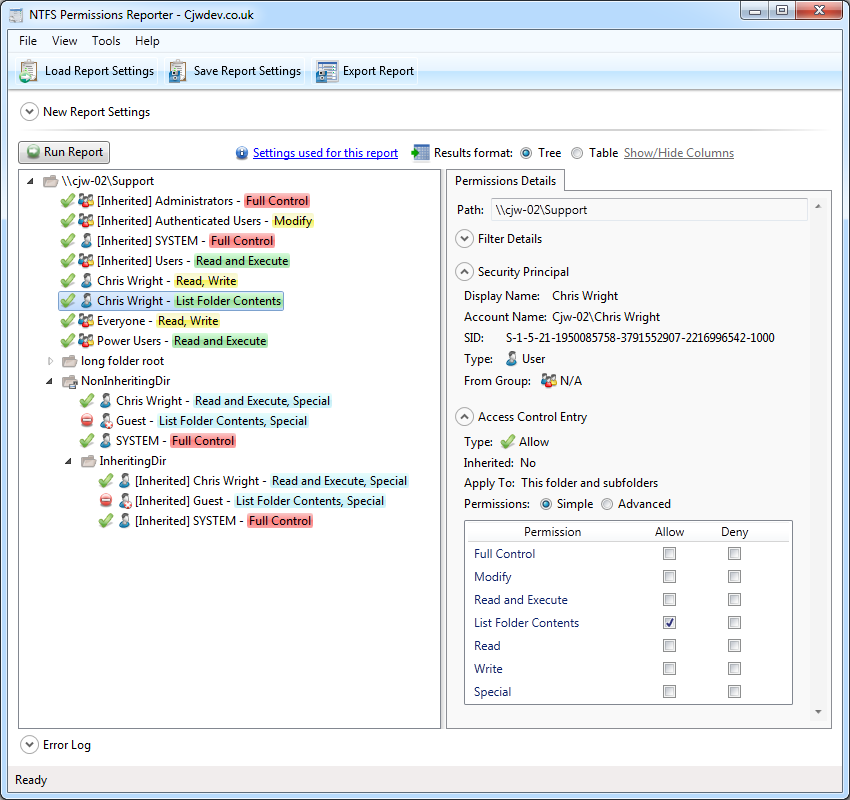
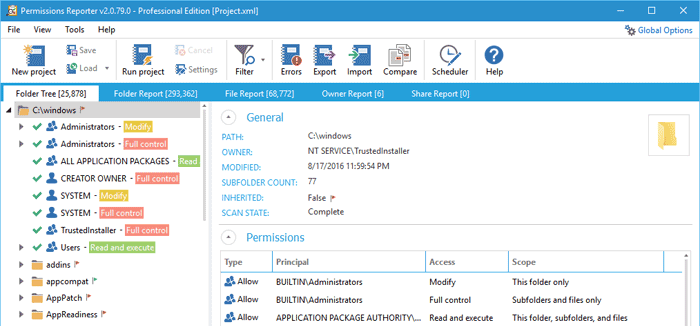
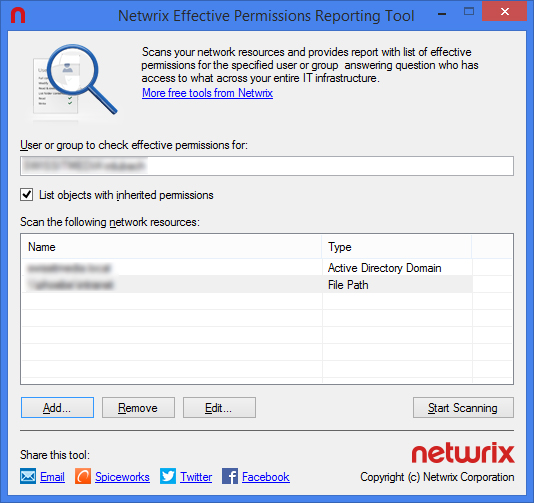
How do you go about that? Well, there is the hard way and the easy way. The hard way is individually going through all the users and groups in your network and recording their permissions. But for me, that is just a waste of time. And you risk making a lot of mistakes. So why not opt for the easy way and use a dedicated permission analyzer tool. With this tool, you don’t need to be connected to the corresponding server and share. Instead, just key in the folder’s UNC path and the name of the group or user on the tool’s UI and it will give you their effective NTFS and share permissions. The Active directory also has built-in security settings you can use but it has one limitation. It only determines the effective permissions and disregard share permissions. In this post we will be highlighting the five best permission analyzers not based on their popularity but what they can do for you. Check out their features and you should be able to find one that’s the best fit. SolarWinds have been making life easy for System admins for the past 10 years thanks to their excellent free and premium networking tools. And while the premium tools offer the best functionality, the free tools also boast of really competitive and useful features. Like the permission analyzer. This is a great tool to not only determine the effective NTFS permissions but also the share permissions for a network share and for a specific user or group. The software is relatively easy to use and with just a few mouse clicks you are able to determine the permission rights that a particular user has. It may not be the best tool for reporting but it gives in-depth visibility into your user and group permissions. You can easily determine how a certain user has inherited their permission by looking at the hierarchical arrangement of the users and groups in your network. The tool also supports nested groups from multiple domains. If your task extends beyond analyzing permissions then you may want to consider the SolarWinds Access Manager. It comes with extra functionalities like the ability to improve security posture, mitigate insider threats, and comprehensive reporting. The name may not be the most memorable but you will definitely not forget this tool. It provides you with an easy way to view NTFS permissions all the way down your directory tree. You can quickly determine which groups have access to which directories and further export the information to an HTML file for further analysis. The standard edition of the software supports more file types like CSV and Excel XLSX. CJWDEV is a tool whose strength lies in its reporting. It has numerous ways to help you sort through the tangled mess of permission, therefore, helping you quickly identify permissions that go against your company standards. When analyzing the permissions in your active directory you can sort the data based on their attributes such as the account name, account SID, whether or not the permission is inherited, account domain, and whether or not an account is active. This tool allows you to view the permissions for both direct and nested groups in your report. And to enable you and others better understand the permissions report, the tool allows you to highlight different permissions with different colours so that there is a clear distinction between them. You can also choose to either display the report in tree form or as a table. This CJWDEV NTFS Permissions Reporter comes with a modern easy to understand interface so that even first time users can easily generate reports a few moments after launching it for the first time. The NTFS Permission reporter is also a great tool to analyze and generate ready to use reports regarding NTFS permission in your Active Directory. It displays the permissions across all folders in a hierarchical manner that you can easily browse through and also includes colour codes to distinguish between different permissions which will help you make a better analysis. You can also choose between tree and table views of the permissions. You will notice a lot of resemblance between this tool and the tool by CJWDEV except that it includes more features. For instance, it has more filter options to better sort through the permissions data. The generated report can be exported to file formats like HTML and MS Excel. This free tool from Netwrix is another tool you can rely upon to analyze permissions in your AD and produce a comprehensive report highlighting who has permission to what. It will help you to ensure that the permission rights of every employee in your organization match with their roles and the report generated will be key in determining the necessary course of action. From the report, you can also tell whether the permissions were explicitly assigned or inherited. But most importantly the reports will be excellent proof to the management and auditors when the need arises. LIZA is a largely unknown tool but is one of the best tools that you can rely upon to facilitate Active Directory Security and perform permission and ACL analysis. It provides a comprehensive review of permissions and audit configurations across the active directory environment. The tool also allows you to track an account and determine where in the directory hierarchy it received the permissions.
The 5 Best NetFlow AnalyzersHow to Fix ‘The Application-Specific Permission Settings do not Grant Local…How to Change and Improve the Fan Curve of your Over-Heating GPU: The Safe and…The ban on TikTok and WeChat will be effective on September 20th